卢本伟病毒样本分析
# 样本信息 
# 静态分析
##1、查壳
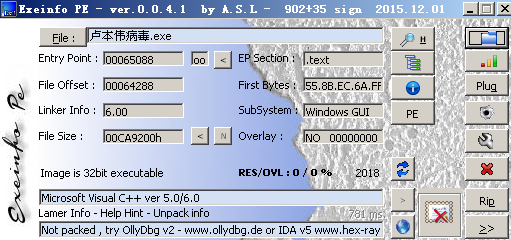
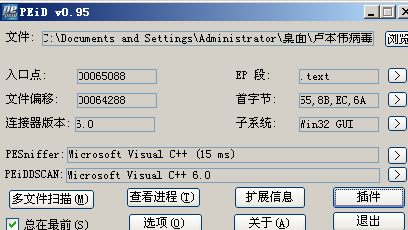
## 2、查看调用了什么算法
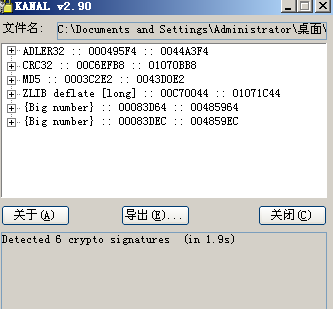
## 3.用IDA打开,可以发现代码逻辑清晰,推测没有加壳


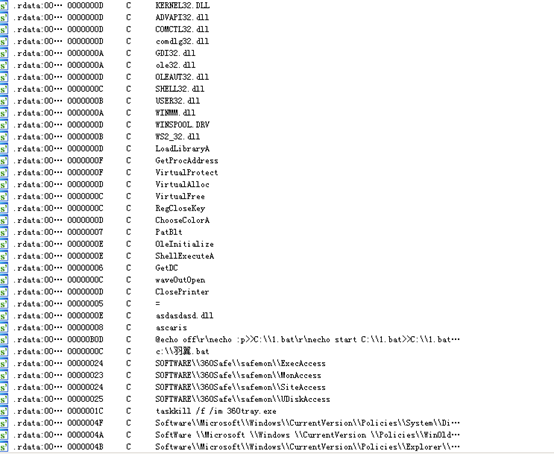
## 4、查看导入表
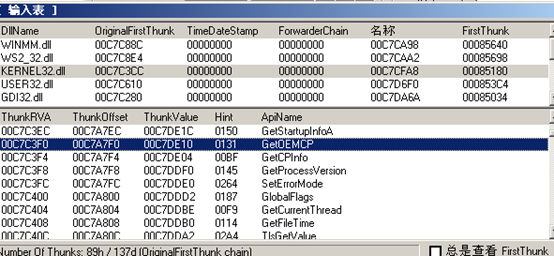
可以在清晰的知道病毒使用ADVAPI32对注册表进行一系列操作
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911221840987.png)
# **动态分析**
## **5**、沙箱运行
**主要特征:设置桌面背景,删除系统文件,命令执行(包括不限于关闭安全服务,注册表操作,修改图标),鼠标设置为错误图标。**
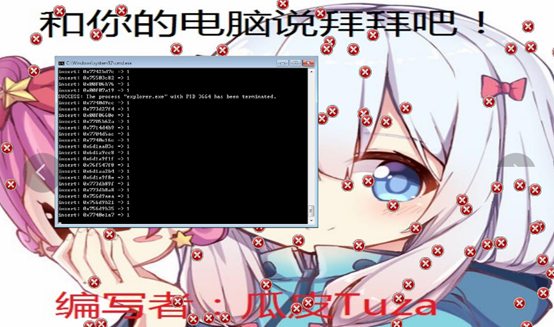
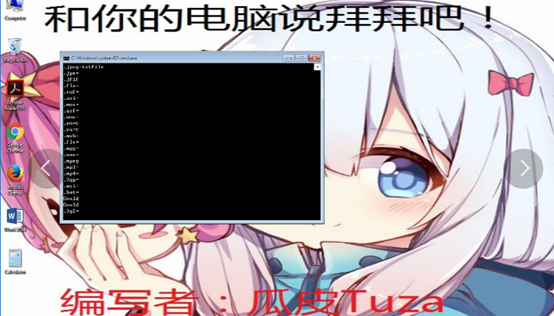
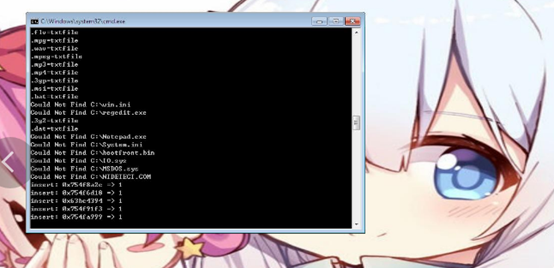
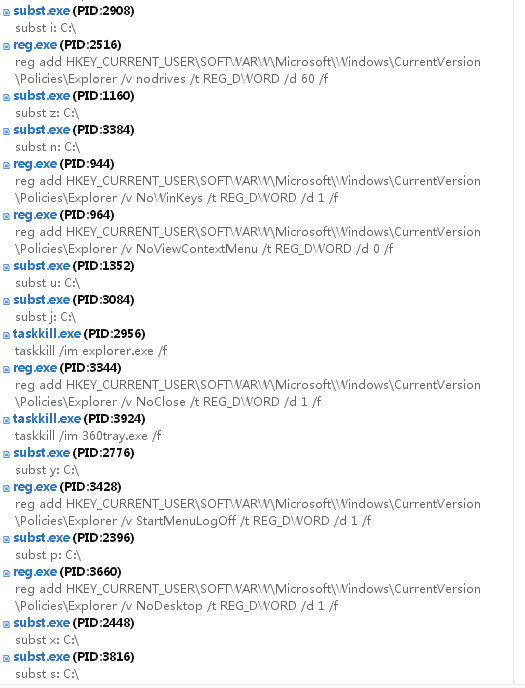
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222119079.png)
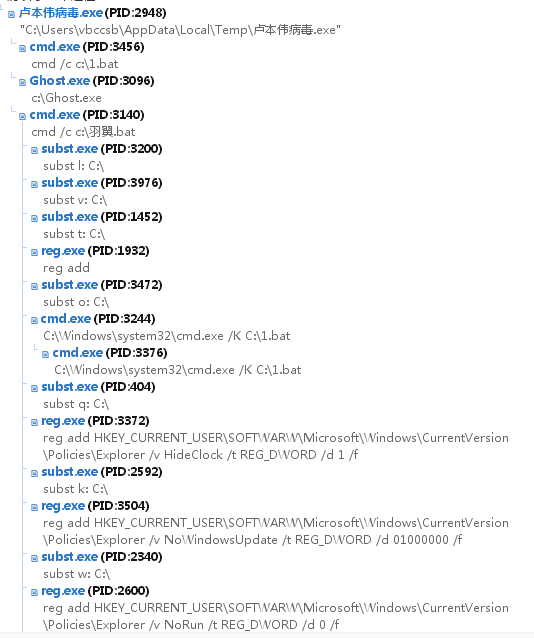
# **病毒分析**
## **start****处分析**
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222156968.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222202610.png)
## **写出文件**
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222207971.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222213083.png)
## **命令行执行**
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222220657.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222225908.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222235625.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222252361.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222304636.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222314449.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222321749.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222334170.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222339453.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222329184.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222349068.png)
## **启动打印机**
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222452347.png)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222502323.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222513290.png)
## **屏蔽快捷键**
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222519726.png)!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222526453.png)
##恶意软件生成内容
Main.cpp内容(从程序导出)
```c
#include <tchar.h>
#include <windows.h>
int WINAPI WinMain (HINSTANCE hThisInstance,HINSTANCE hPrevInstance,LPSTR lpszArgument,int nCmdShow)
{
HWND hwnd = GetDesktopWindow();
HDC hdc = GetWindowDC(hwnd);
POINT point;
while(1)
{
GetCursorPos(&point);
DrawIcon(hdc,point.x,point.y,LoadIcon(NULL, IDI_ERROR));
Sleep(10);
}
}
```
Ghost.exe:
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222538808.png)
Drawerror.exe:顾名思义就是在鼠标经过的地方出现error图标(由main.cpp编译而来)
!(https://pdc246871-1302651496.cos.ap-nanjing.myqcloud.com/image-20200911222544733.png)
# 总结
新手分析病毒,如有错误欢迎指出。
https://pan.baidu.com/s/1S45g40UXdKGiGapOduiv8w
提取码:52po 还以为是桌面图标全改成LBW,然后壁纸替换,无限弹窗LBWNB,结果这和LBW打不到一块啊。。。。不过这波分析可以,LBWNB! 你17张牌能秒我话说你这个病毒样本在哪儿找到的 请问为啥叫卢本伟病毒? 请问为啥叫卢本伟病毒?
看到卢本伟我进进来了 应为这个软件被 挂了 度 而这个软件是他做的 全体起立 LBYNB LBW病毒可还行,请问为啥叫这个名,和LBW有啥关系{:1_904:} 我经常说一句话:当年,陈刀仔用20块赢到3700万,我卢本伟用20万赢到500万不是问题。
LBW病毒NB